Start Using PagerDuty Today
Try PagerDuty free for 14 days — no credit card required.
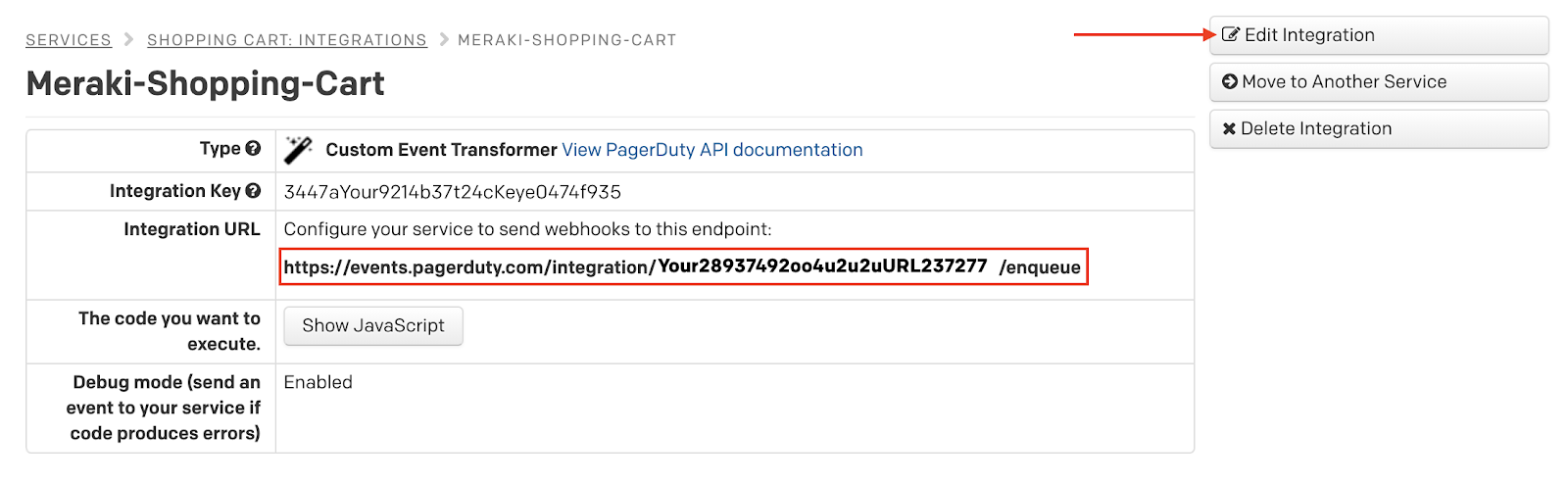
4. Next, click Edit Integration and replace the JavaScript code in the editor with the following code and click Save changes:
// Consume Meraki Alert via Webhook var body = PD.inputRequest.body; // Set Alert Severity var severity = "warning"; // critical // error // warning // info // unknown if(body.alertType == "Settings changed") {severity = "info";} if(body.alertType == "Motion detected") {severity = "info";} if(body.alertType == "Network usage alert") {severity = "warning";} if(body.alertType == "APs went down") {severity = "critical";} if(body.alertType == "Uplink status changed" && !body.alertData.uplink) {severity = "critical";} // Format payload var cef_event = { event_type: PD.Trigger, description: body.alertType, severity: severity, source_origin: body.networkId, dedup_key: body.alertId, service_group: body.organizationId, event_action: PD.Trigger, details: body } PD.emitCEFEvents([cef_event]);
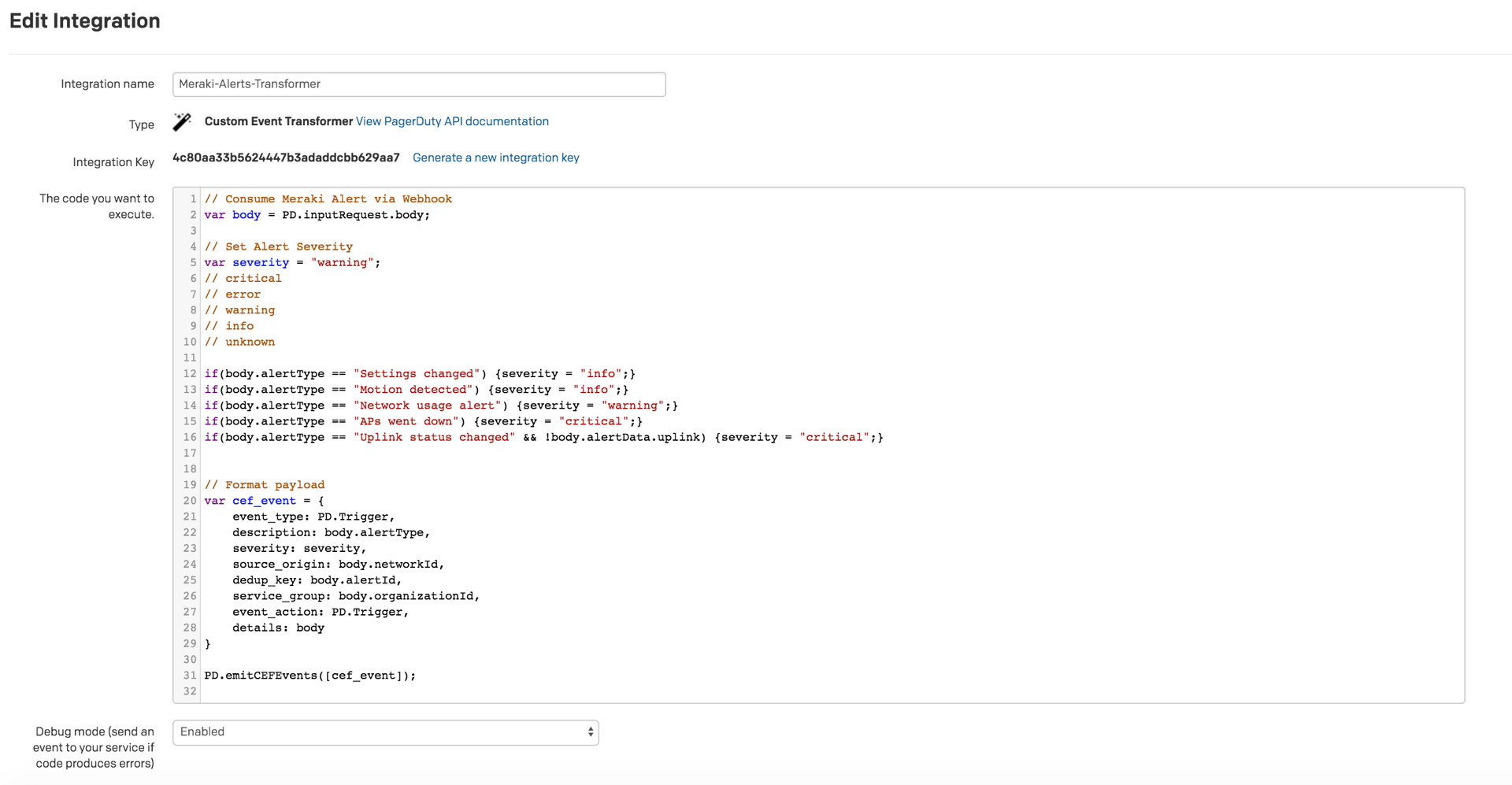
The above code captures the alert data via a JSON post. The data is then parsed and a severity type is assigned to a specific alertType. These can be adjusted or removed entirely if desired.
Another option is to include logic here to filter out messages based on the body.sharedSecret to match a user defined password. Simply replace the last line of code with this:
// Check secret and store event const SECRET = "asdf1234"; if(body.sharedSecret == SECRET){ PD.emitCEFEvents([cef_event]); }
5. Select the Organization and Network you would like to work with.
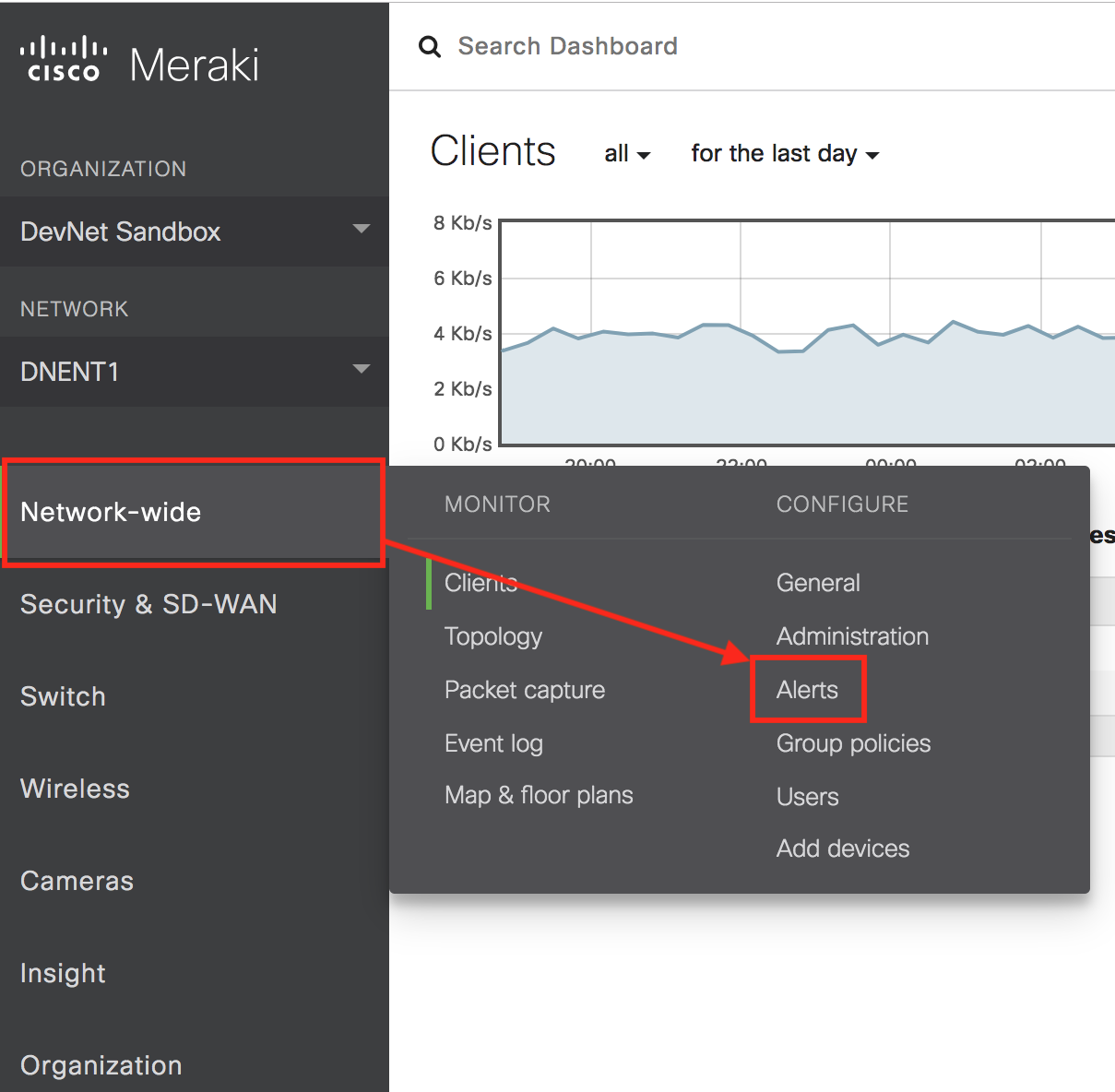
6. In the Network-wide menu and under Configure, click Alerts. Choose your desired alert settings here. You can use Cisco Meraki to Alert for events such as things like whether “A VPN connection comes up or goes down”, “Malware is downloaded”,. “A power supply goes down”, and more.
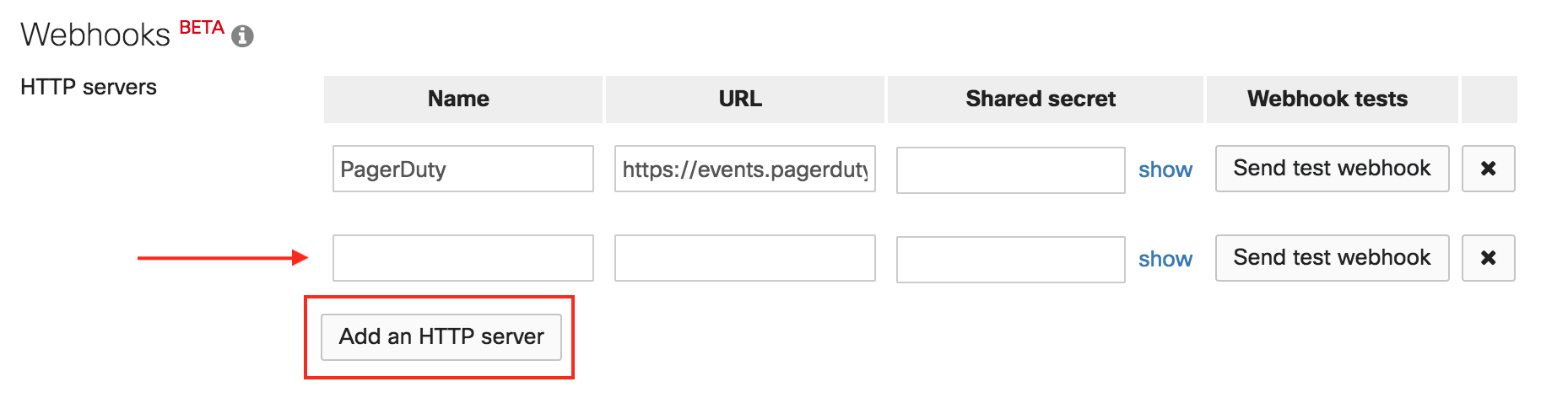
7. Under the Network-wide menu, scroll to the Webhooks section and click Add an HTTP server.
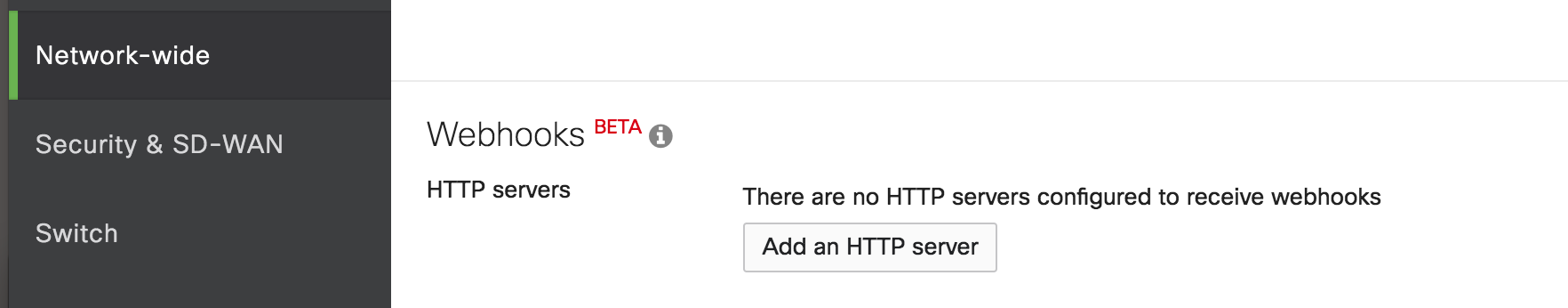
8. On the Webhooks screen, use the events API Integration URL (generated in step 5 of the In PagerDuty section above) and paste it in the URL field. Name the Webhook “PagerDuty”. You do not need to input anything into the Shared secret section.
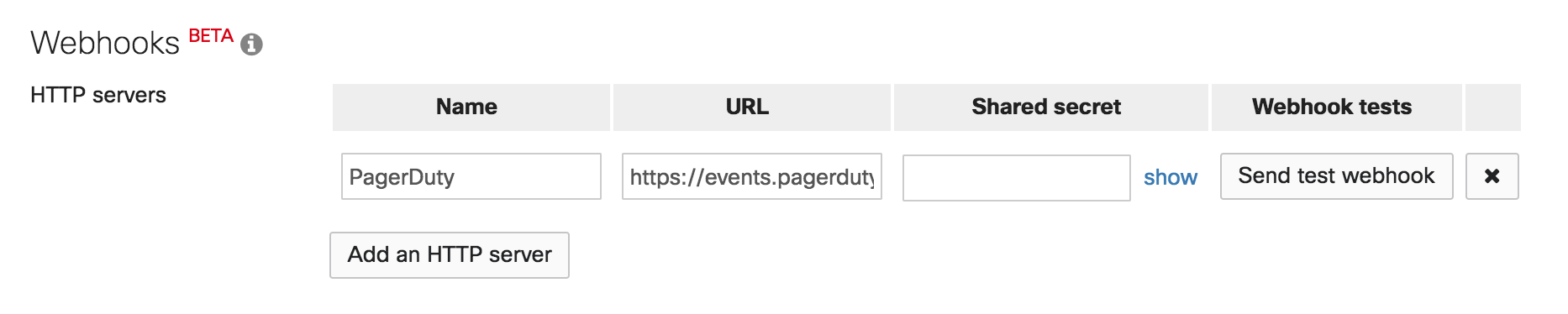
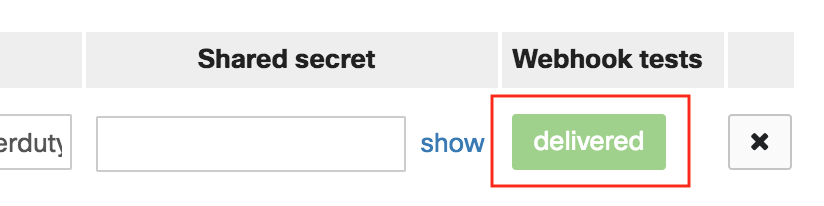
9. You should now be able to test by hitting the Send test webhook button. If connected properly, the button will turn green and say delivered. If it says failed, check your URL and try again.
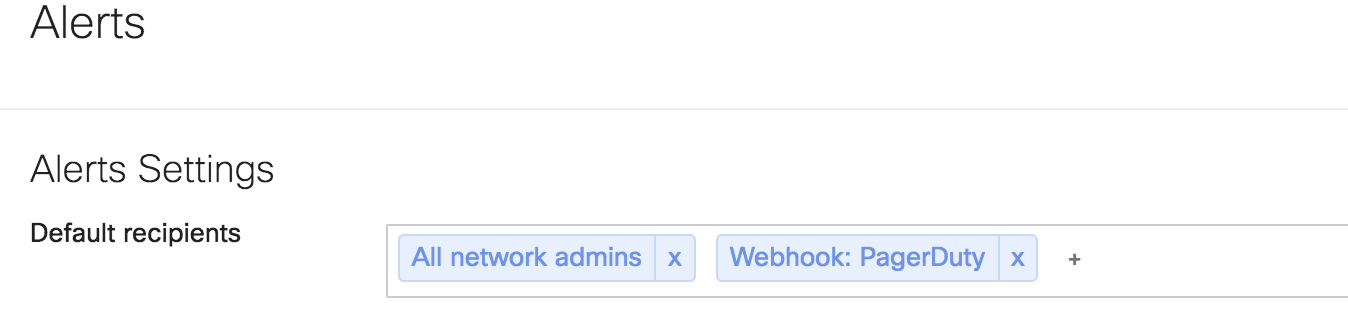
10. Scroll back up to the top of the Alerts page and set the new PagerDuty Webhook as a default recipient.
11. Finally, at the bottom of the screen, click Save.
12. Under Incidents → Alerts, you should now see an alert that was generated when you clicked the test button in Meraki Alerts.
Yes, simply click Add an HTTP Server in the Webhooks section in Meraki Alerts and follow from Step 4 of the In Meraki section above
No, you will still need to resolve incidents in PagerDuty.
Try PagerDuty free for 14 days — no credit card required.