Start Using PagerDuty Today
Try PagerDuty free for 14 days — no credit card required.
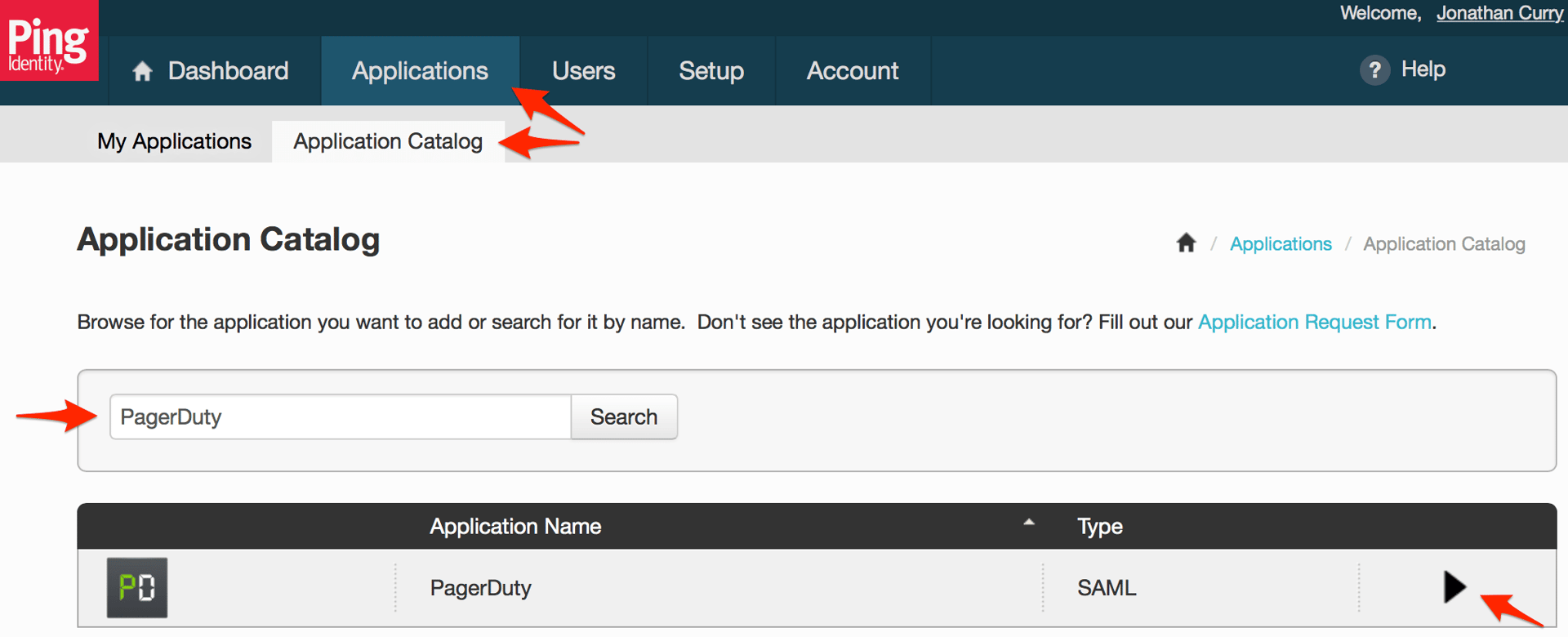
PingOne is a single-sign on provider, which makes it easy to manage your SaaS application logins and permissions. PagerDuty is available within the PingOne app catalog. This makes it easy to manage access to your PagerDuty account. Follow this simple guide to get your PingOne account tied to your PagerDuty account.
You must be the Account Owner of your PagerDuty account in order to make these changes. Additionally, SSO capabilities within PagerDuty are only available on our Business and Digital Operations plans. Please contact our sales team if you are interested in upgrading your plan.
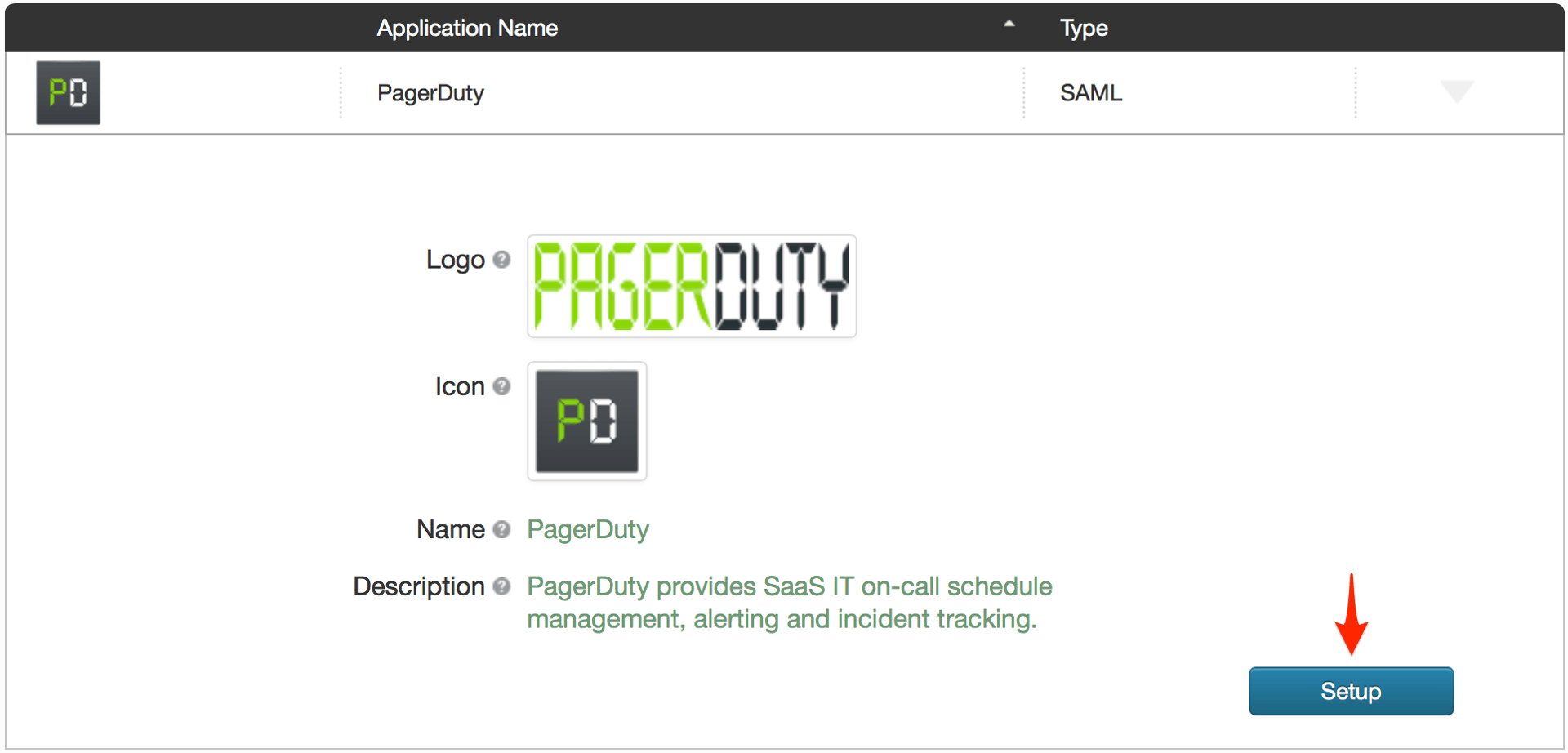
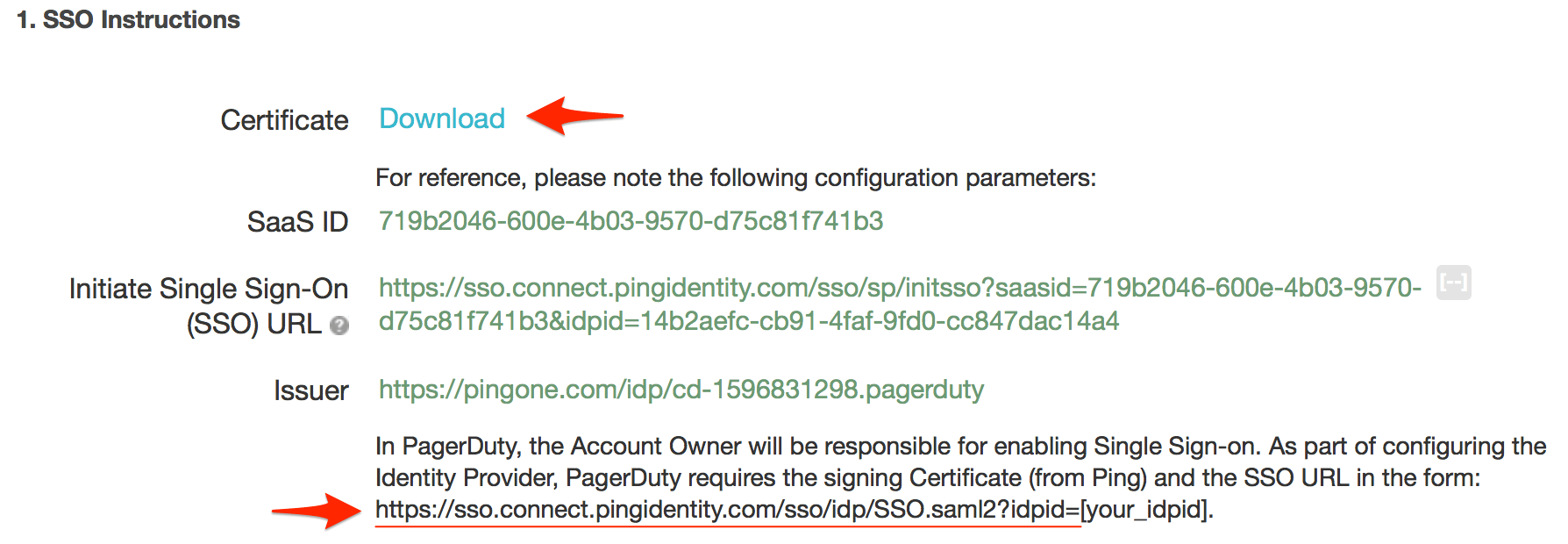
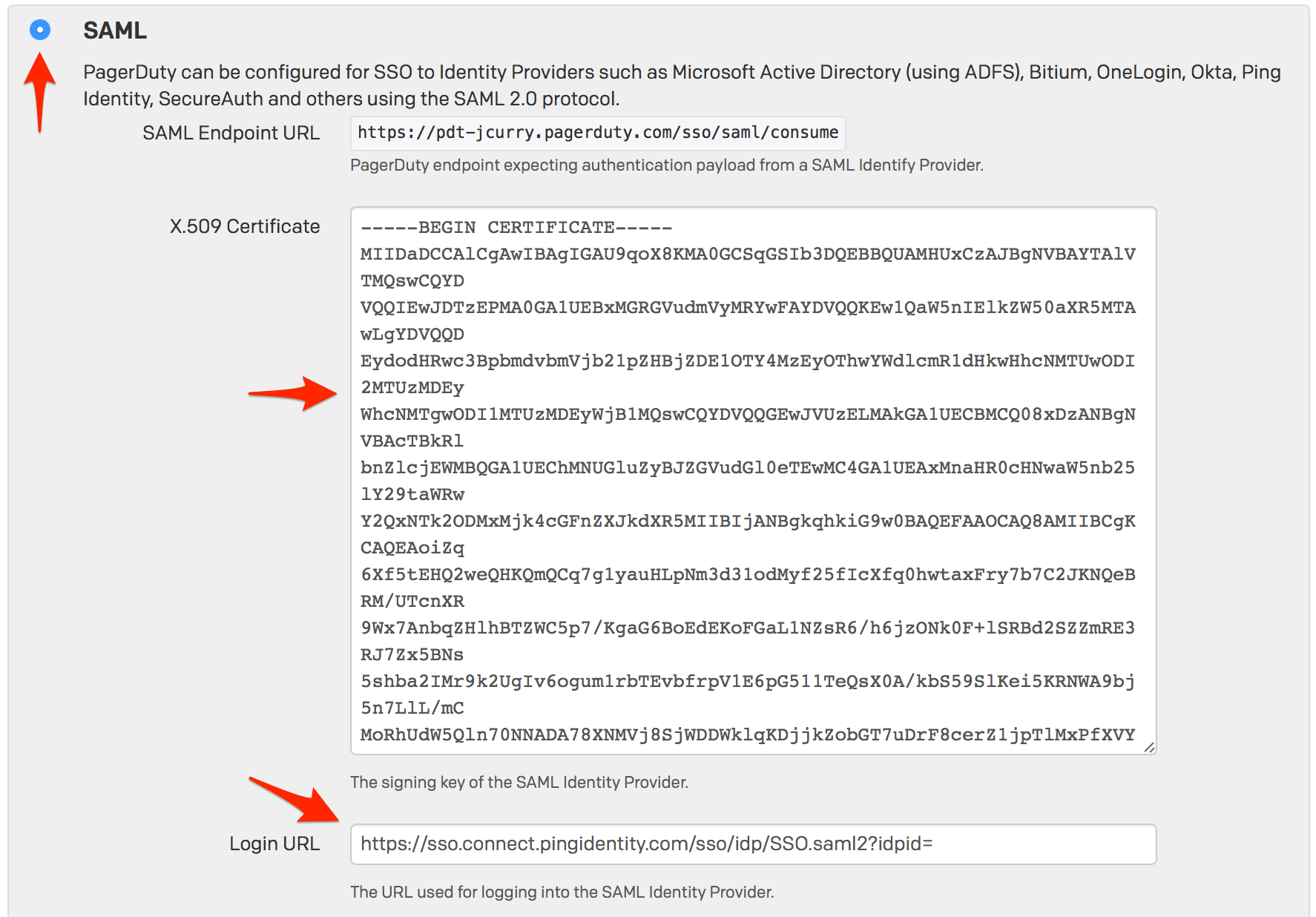
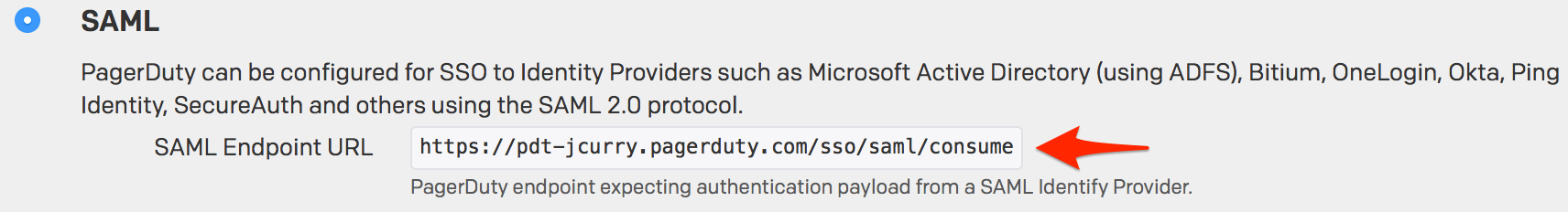
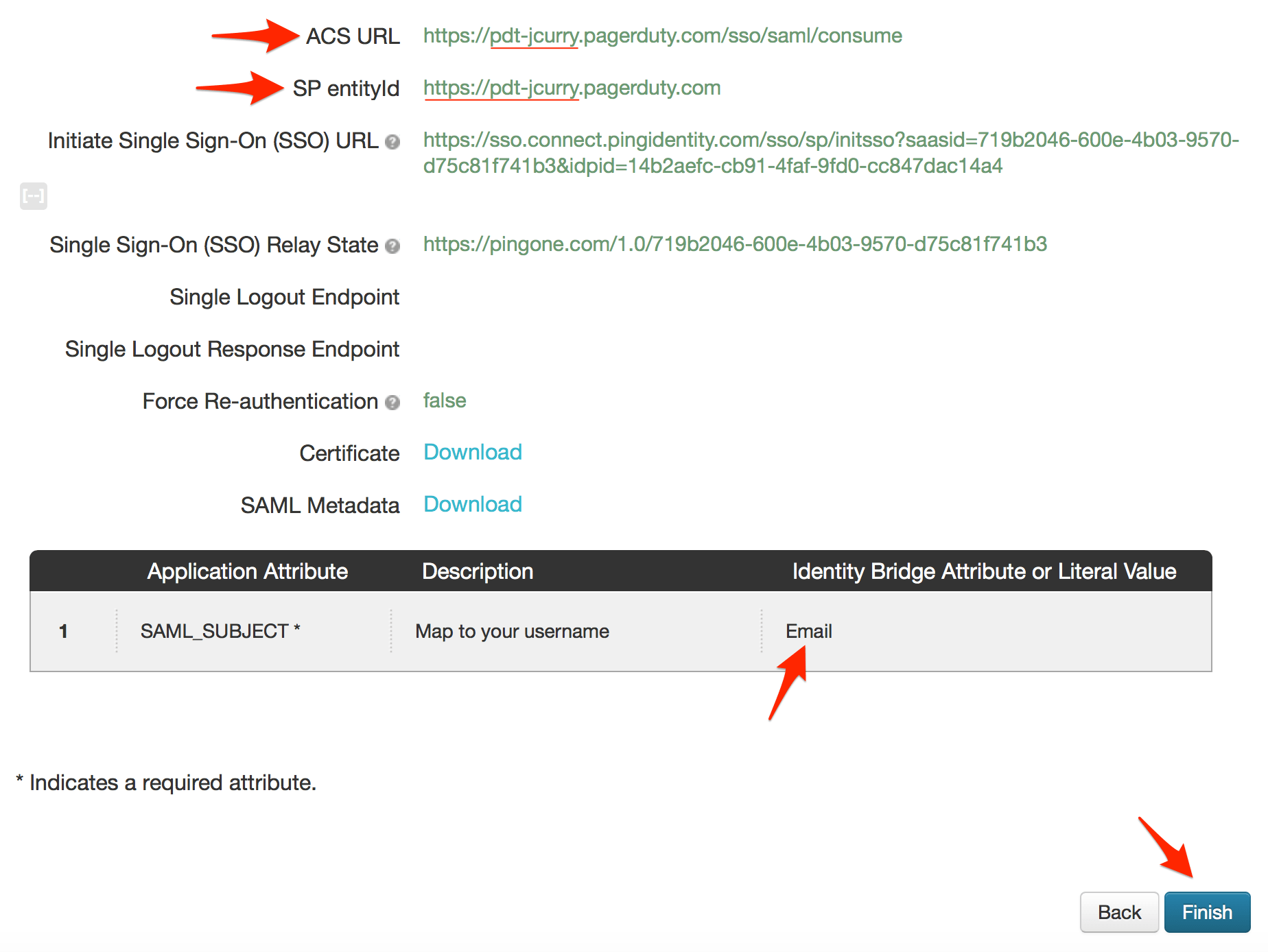
${accountid}.pagerduty.com in the Entity ID field by default and provides instructions to simply replace ${accountid} with your PagerDuty subdomain. Unfortunately replacing only ${accountid} with your subdomain will not work; you must also enter https:// before your subdomain.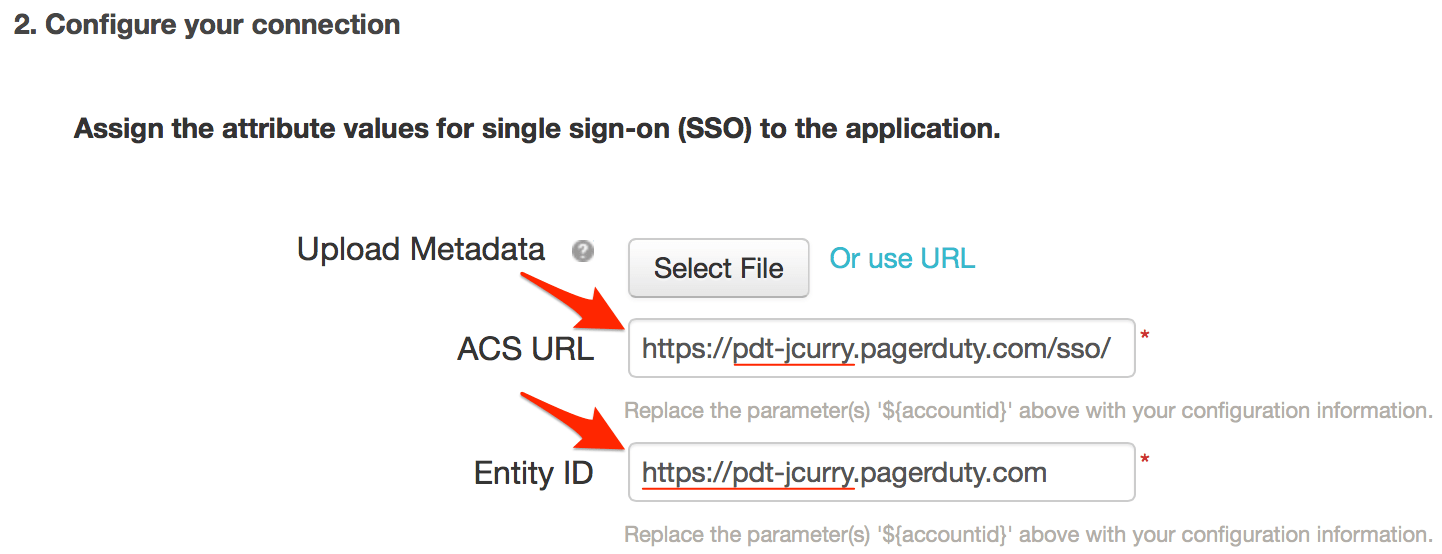
https://sso.connect.pingidentity.com/sso/sp/initsso?saasid=00000000-abcd-0000-efgh-xyz123456789&idpid=11111111-xxxx-1x1x-1111-xxxx1111xx1111111111-xxxx-1x1x-1111-xxxx1111xx11
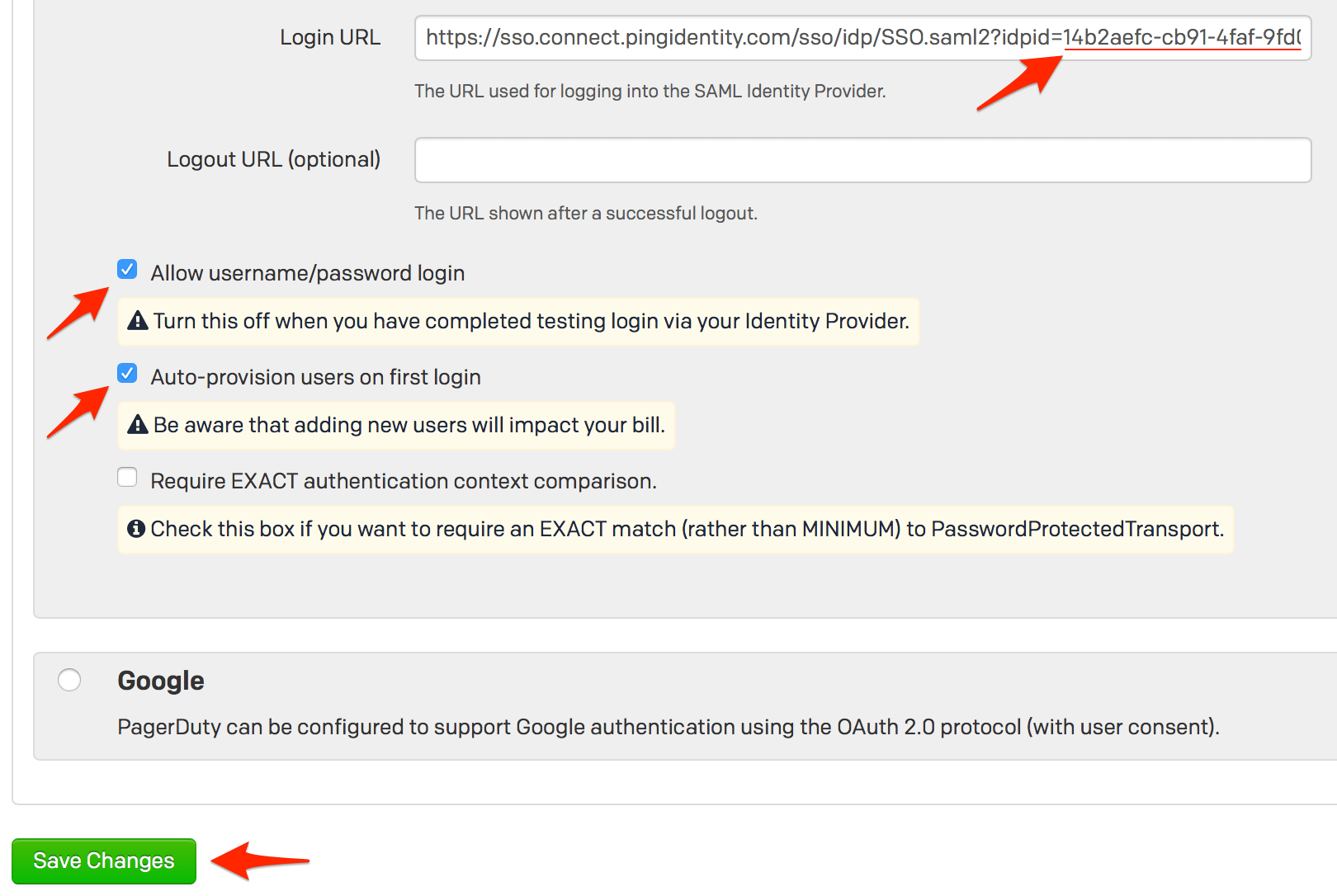
Click Continue to Next Step after you have copied the idpid parameter.
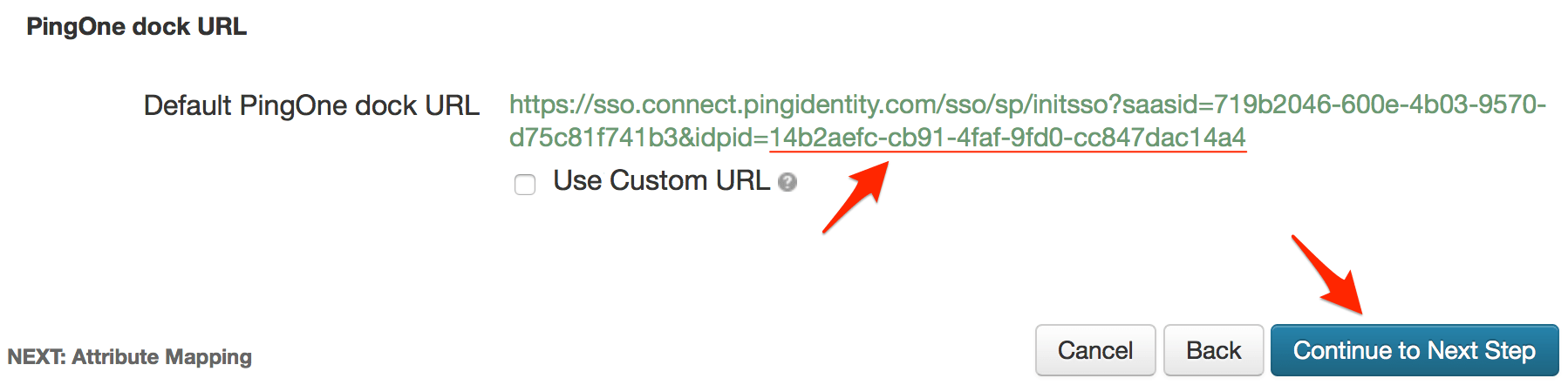
11111111-xxxx-1x1x-1111-xxxx1111xx11, the Login URL in PagerDuty should be set to this:
https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=11111111-xxxx-1x1x-1111-xxxx1111xx11
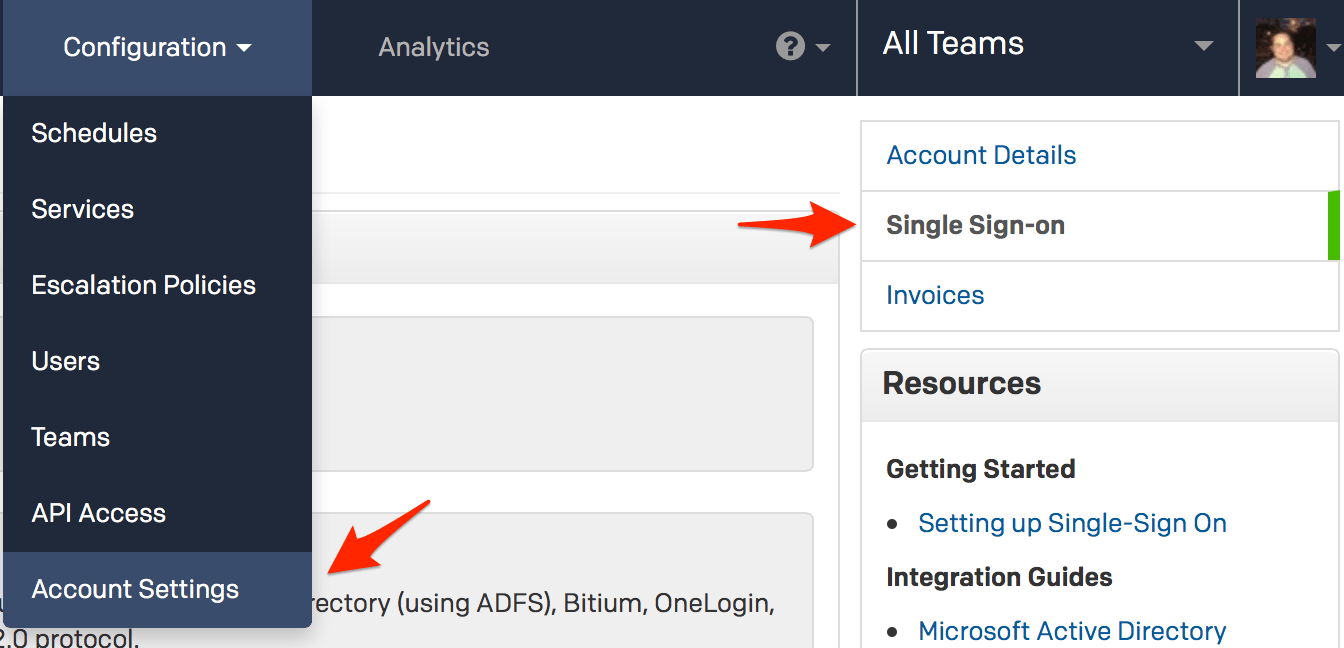
When you complete the steps in this guide and are done testing, you can return to this page to disable user logins via username and password.
With auto provisioning enabled, you can allow SSO users to create a PagerDuty account without manual intervention, however please keep in mind that adding additional users will affect your billing if you go over the number of users included in your pricing plan.
Click Save Changes when you are done on this page.
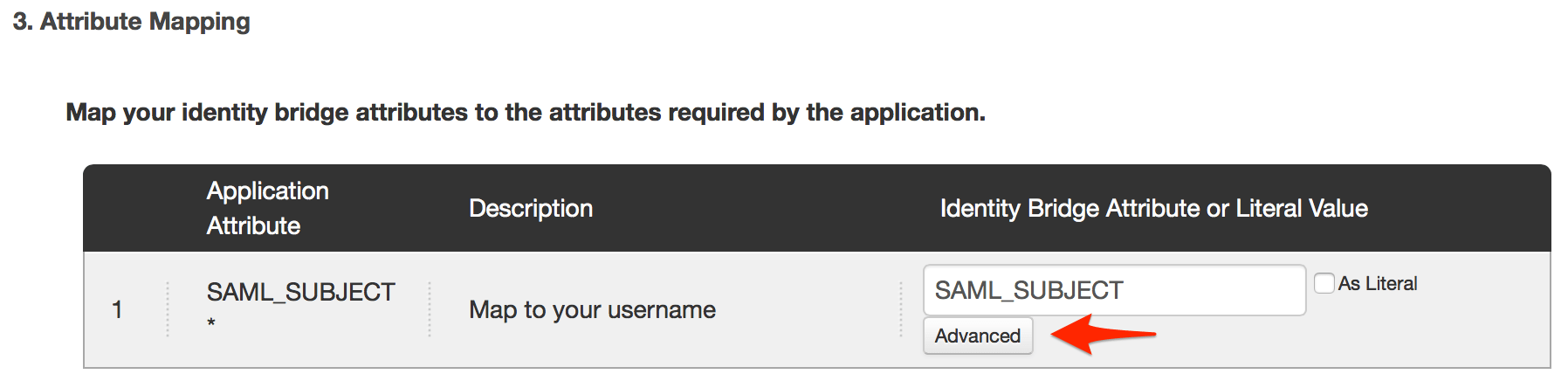
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, and set the IDP Attribute Name or Literal Value to Email, then click Save.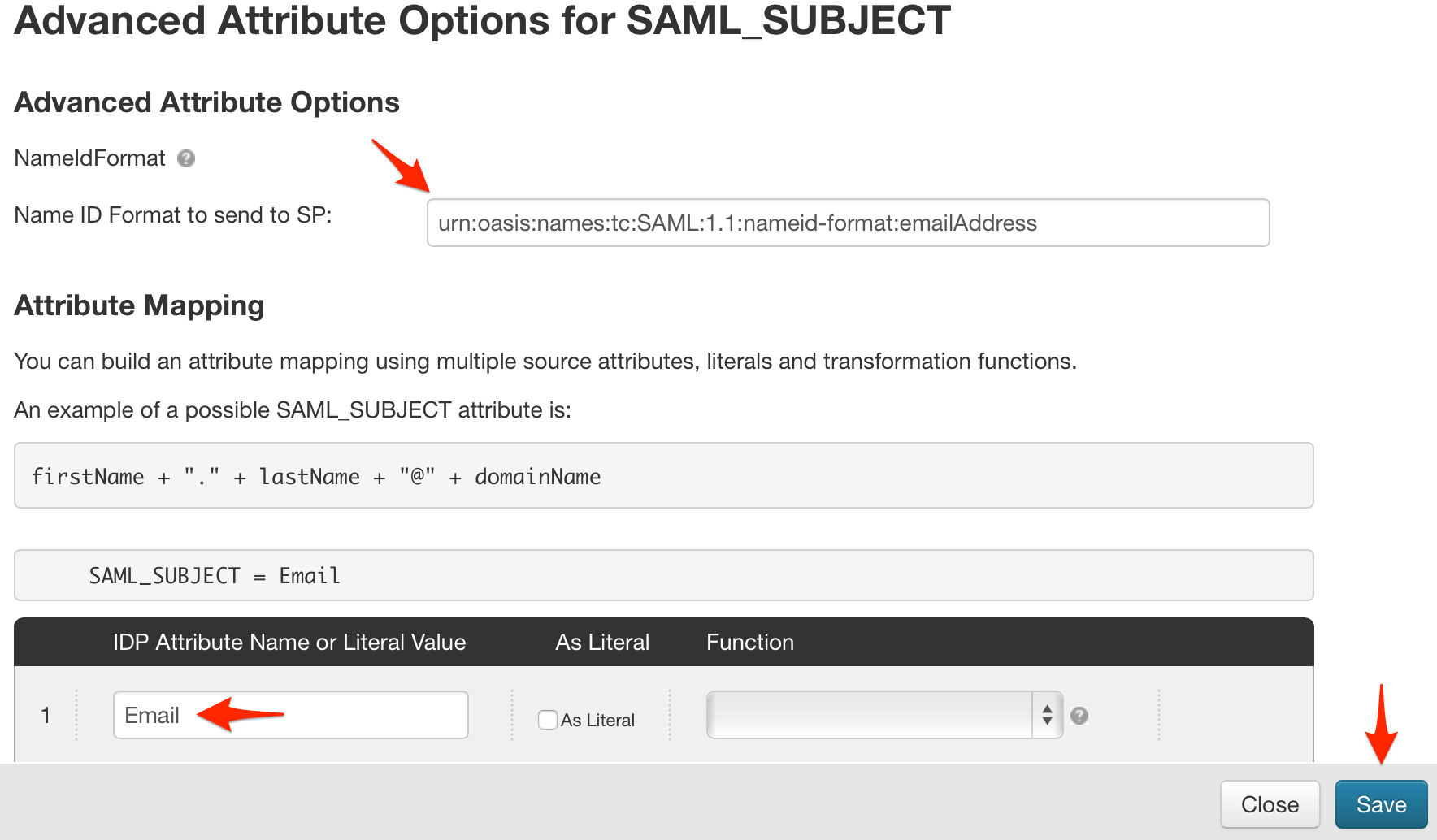
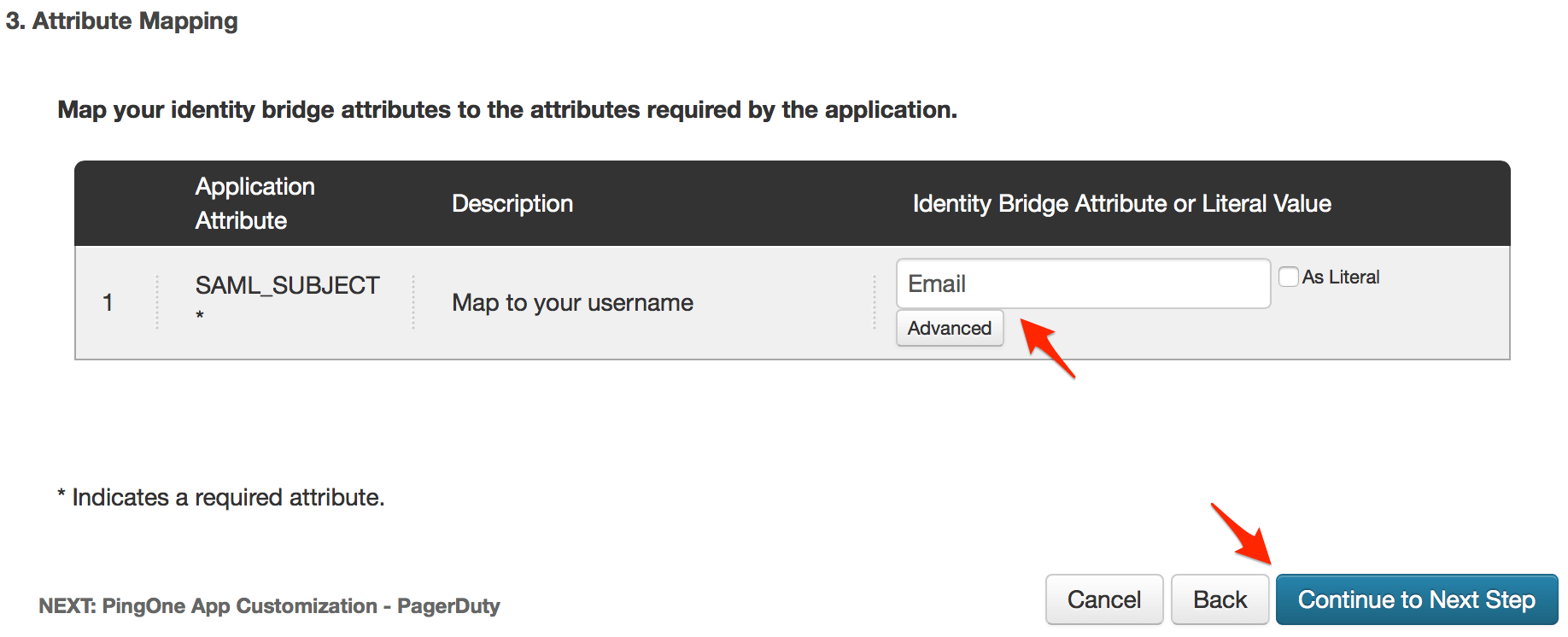

Even with username and password authentication disabled for users, the Account Owner will always be able to login with their username and password as a backup option should you need to change the SSO configuration or disable it completely.
SSO is only available in accounts on our current Standard or Enterprise plans. Please contact our sales team if you are interested in upgrading your plan.
Try PagerDuty free for 14 days — no credit card required.