Start Using PagerDuty Today
Try PagerDuty free for 14 days — no credit card required.
Watcher is the alerting and notification product for Elasticsearch that lets you take action based on changes in your data. It is designed around the principle that if you can query something in Elasticsearch, you can alert on it. Simply define a query, condition, schedule, and the actions to take, and Watcher will do the rest.
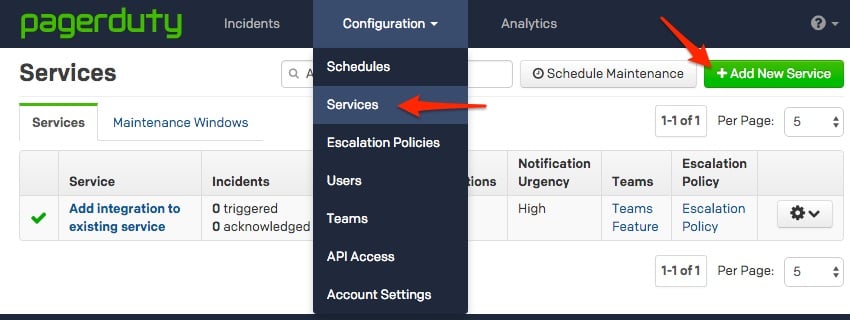

If you are creating a new service for your integration, in General Settings, enter a Name for your new service. Then, in Incident Settings, specify the Escalation Policy, Notification Urgency, and Incident Behavior for your new service.
The watcher state in the response should read started:
curl -XGET 'http://localhost:9200/_watcher/stats?pretty'
Note: The watch below is set to always execute every 10 seconds for testing purposes. In most production environments you will want to update the trigger and condition to only execute the action when there is an issue to reduce noise. You may also want to add a throttle period to your PagerDuty action to prevent duplicate triggers in PagerDuty. You can find detailed instructions on configuring each aspect of your watches in the Elastic Watcher Documentation.
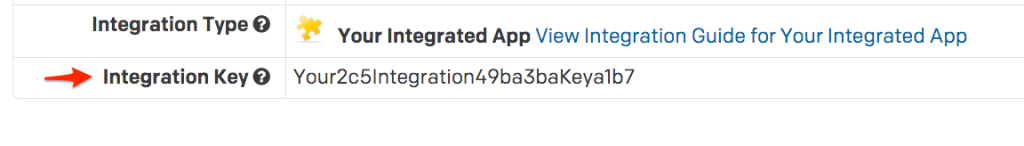
Make sure to update the service_key in the body of the action with the integration key you copied in step 5 above:
curl -XPUT 'http://localhost:9200/_watcher/watch/cluster_health_watch' -d '{
"trigger" : {
"schedule" : { "interval" : "10s" }
},
"input" : {
"http" : {
"request" : {
"host" : "localhost",
"port" : 9200,
"path" : "/_cluster/health"
}
}
},
"condition" : {
"always" : {}
},
"actions" : {
"pagerduty": {
"webhook": {
"scheme": "https",
"method": "POST",
"host": "events.pagerduty.com",
"port": 443,
"path": "/generic/2010-04-15/create_event.json",
"body": "{\"service_key\": \"ENTER_YOUR_SERVICE_KEY_HERE\",\"event_type\": \"trigger\",\"description\": \"Issue in elastic watcher\"}",
"headers": {"Content-type": "application/json"}
}
}
}
}'
Yes, when defining your action for any of your watches you can specify the event_type in the body of your request. This attribute must be one of trigger, acknowledge, or resolve.
Yes, this is easy to accomplish with the current integration. All you would need to do is define multiple watches or multiple actions within your watch that contain the different integration keys.
You can check the watch history or status_index to see what actions have been performed when your watch conditions are met:
curl -XGET 'http://localhost:9200/.watch_history*/_search?pretty' -d '{
"query" : {
"match" : { "result.condition.met" : true }
}
}'
If this request does not produce any results, your watch has not yet had its condition met and no actions would have been triggered.
In this scenario there is an issue with the parameters you defined for the PagerDuty action. Some of the most common issues we encounter are:
Try PagerDuty free for 14 days — no credit card required.