Invisible Security at the Speed of Cloud
Security teams have the tough job of monitoring and securing every single workload in each cloud and for workloads in the development pipeline. Inevitably, these processes wind up being a bottleneck from the developer’s perspective, and developers get frustrated. Understandably, developers feel like security is simply making their jobs harder. But, on the other hand, security teams feel like they’re powerless to provide full coverage.
The perfect world would be where cloud security is invisible, deployed seamlessly across all workloads without impacting cloud performance. But how realistic is it to achieve this today?
Evolution of Security Visibility
There are several types of tools to increase security visibility while decreasing the friction between software development, operations, and security.
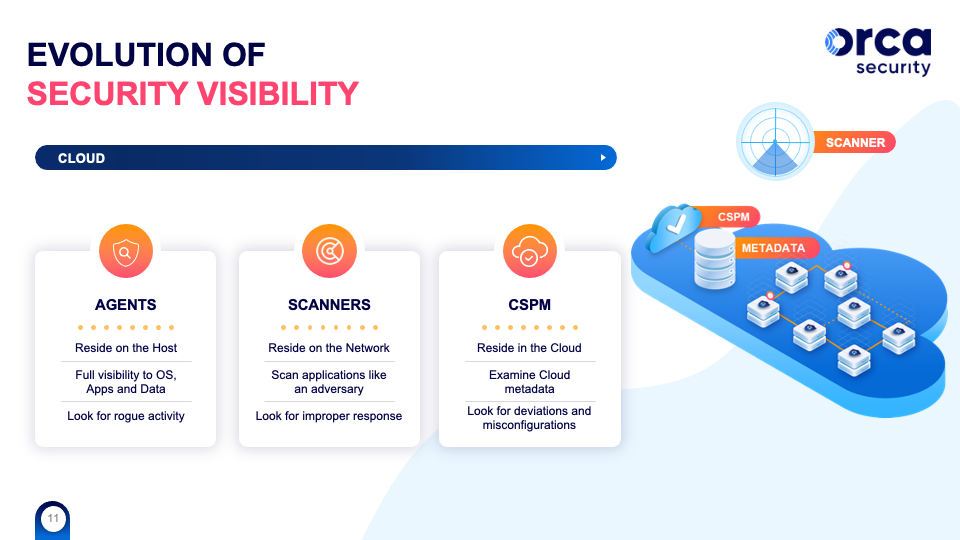
- Agents: Agents are installed and maintained as an application that runs parallel to custom-built workloads, providing visibility into what is running on each host.
- Network Scanning: Scanners probe resources externally, looking for known configuration errors and other vulnerabilities.
- CSPM: Cloud Security Posture Managers monitor cloud configurations and analyze security service configurations, including virtual machines, networks, storage buckets, and more. CSPMs rely on agent-based solutions to peer inside workloads resources to measure risk.
- CWPP: Cloud Workload Protection Platforms measure workload-specific risks like software vulnerabilities, malware and host or container-based misconfigurations.
Despite the availability of these offerings, there are challenges associated with each. Most importantly, using any one tool in a silo reduces the context of the broader security scenario. Without adequate context, security alerts cannot be prioritized in a truly useful manner.
Context is Key to Determining Risk
Without understanding the complete context of a given cloud environment, it is difficult for cloud security teams to understand security issues and then triage alerts quickly. Moreover, each of the aforementioned visibility tools has its own context-related limitations:
- With an agent-based approach, adding the necessary context to alerts falls on the security team. However, when you take into consideration these teams are typically responsible for managing tens or hundreds of cloud accounts across thousands of resources, applying proper context at the workload level using alerts alone is impossible.
- Network Scanners only provide a partial solution to cloud security; they have “blind spots” and either don’t see all cloud assets or can’t analyze assets in-depth.
- CWPP platforms integrate per asset; hence their ability to understand each workload’s context is minimal.
- CSPM only has perspectives on security controls, not the underlying data.
Security Alerts “Gone Wild”
The most significant factor contributing to “alerts gone wild” is that most cloud security approaches consider just one dimension of risk; the severity of the underlying security issue. But, ignoring the underlying issues invariably ends up treating your cloud as a long list of alerts that lack context, causing alert fatigue. But understanding risk is much more serious, involving:
- Severity: how significant is the underlying security issue?
- Exposure: who can take advantage of the security issue?
- Blast radius: what is the potential impact on the business?
If we think of risk pragmatically, we get a much more accurate view of just how severe any given risk truly is.
Use Case: How Context Helps Your SOC Sleep Better at Night
The following illustrates how context can help. Server 1 and Server 2 are both running a web server that uses a library vulnerable to remote execution with a high CVE score.
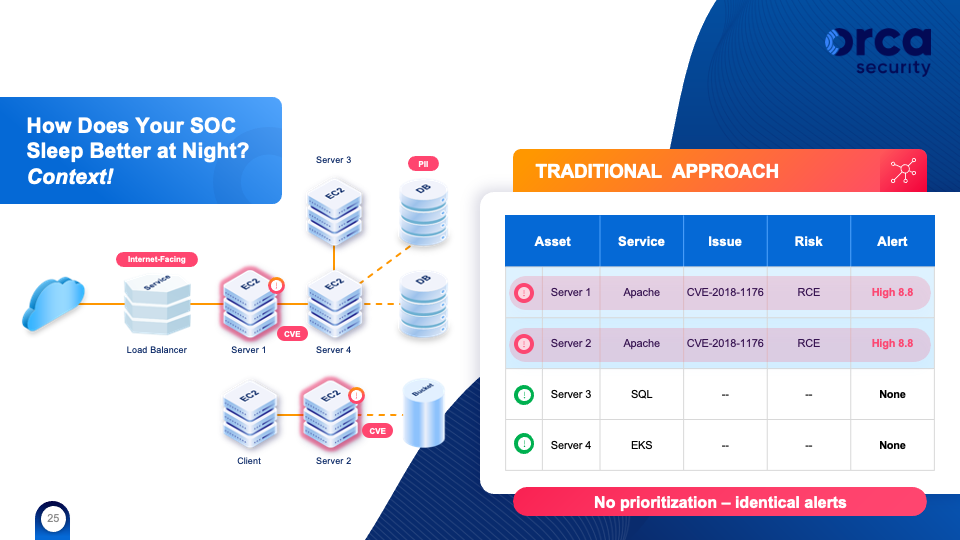
A context-less approach would report this vulnerability with a static CVSS score. Thus, both workloads will end up getting the same score and risk categorization. In theory, the same amount of time will be spent on each of these alerts.
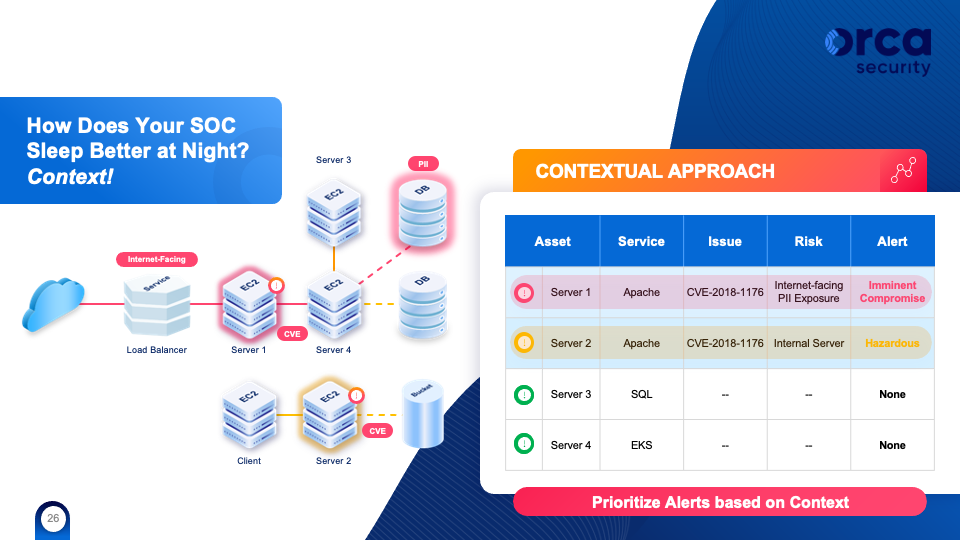
What if we also consider the environmental context? We can tell the service on Server 1 is Internet-facing and, therefore, the risk is classified as an imminent compromise. Server 2 is not Internet-facing and can’t be reached directly from anywhere but another host. So, the risk level is downgraded down to Medium.
This example serves to illustrate that context is mandatory in any security strategy. With thousands and thousands of alerts, you need to know which ones would likely lead to compromise and require action now versus those that can wait.
Orca Security: Dramatically Increases the Effectiveness of Your Security Team

Orca Security’s purpose-built cloud security platform discovers both workload and cloud risks and uses observations from either side to inform risks found in the other. When Orca finds software vulnerabilities on a host, several contextual factors are considered:
- Cloud network accessibility
- Age of the vulnerabilities known
- Exploitation paths and more.
All information is used to score each alert, reducing the many alerts to the important few.
PagerDuty + Orca Security
Orca Security empowers devops teams using PagerDuty’s extensive platform for digital operations management to build and release software quickly without compromising on security. Utilizing Orca Security’s SideScanning™ technology, devops teams enjoy a zero-touch approach to cloud security that provides complete and comprehensive visibility and coverage. Orca Security will identify risks both deep within your workloads and broadly across all of the cloud services you leverage and pass those contextually-risked alerts to PagerDuty to provide unified visibility and ultimately action and resolution.
Integration Benefits
- Notify on-call responders based on alerts sent from Orca.
- Create alerts of different severity based on contextual findings from Orca.
- Alerts in PagerDuty will be resolved when Orca observes the issue in question has been resolved in the respective cloud account.
How it Works
- Orca Security constantly scans your workloads and cloud configuration. Any identified risks will send an event to a service in PagerDuty.
- Once the issue has been resolved and realized in Orca, a resolve event will be sent to the PagerDuty service to resolve the alert, and associated incident on that service.
- Alerts from Orca Security will trigger a new incident on the corresponding PagerDuty service.
Come and view the on demand video at PagerDuty Virtual Summit 2021, “Invisible Security At The Speed Of Cloud” presented by Patrick Pushor, Technical Evangelist, Orca Security. You can register for the event to view the on demand session!
To learn more about the Orca Security and PagerDuty Integration, visit https://www.pagerduty.com/integrations/orca-security/.


